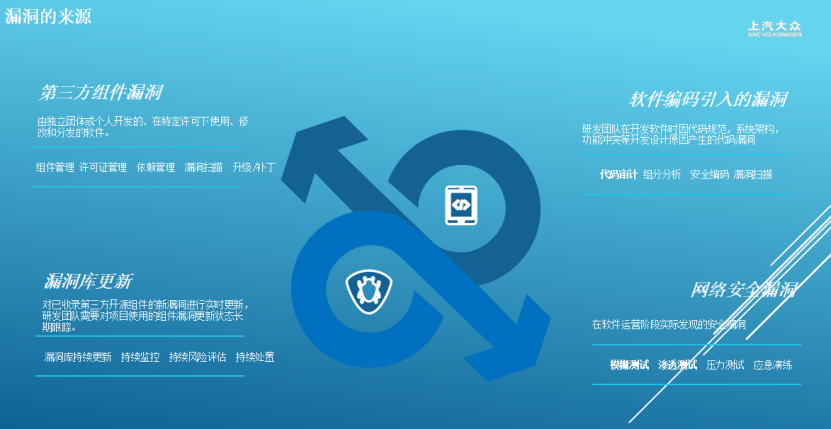
The automotive industry is accelerating its transition to intelligent systems, and the security risks posed by vehicle vulnerabilities are becoming increasingly apparent. As in-car software becomes more complex, traditional reliance on passive defensive and management measures is becoming less effective against new types of security threats. In this context, a proactive design-centered vulnerability defense system will become a future trend, aiming to avoid risks from the source and build a more solid defense for vehicle system security. Wu Jianjian, the cybersecurity manager at SAIC Volkswagen, elaborated on the importance of cybersecurity, the current regulatory status, and response measures. He pointed out that in recent years, the number of security vulnerabilities has risen sharply, with a shortened window for exploiting high-risk vulnerabilities and more organized attack behaviors, making it imperative to address automotive vulnerabilities for industry development. Wu further analyzed the sources of vulnerabilities and introduced classification and grading measures, emphasizing that these are foundational prerequisites for establishing a reasonable vulnerability management mechanism.
The severity and uniqueness of automotive vulnerability protection are underscored by the ongoing intelligent transformation in the automotive industry, which faces increasingly severe threats from vulnerabilities. Automotive vulnerabilities differ significantly from IT vulnerabilities; due to the high speeds at which vehicles operate, the potential damage or threats from automotive vulnerabilities far exceed those of IT vulnerabilities. Additionally, the repair cycle for automotive vulnerabilities is considerably longer than that for IT products.
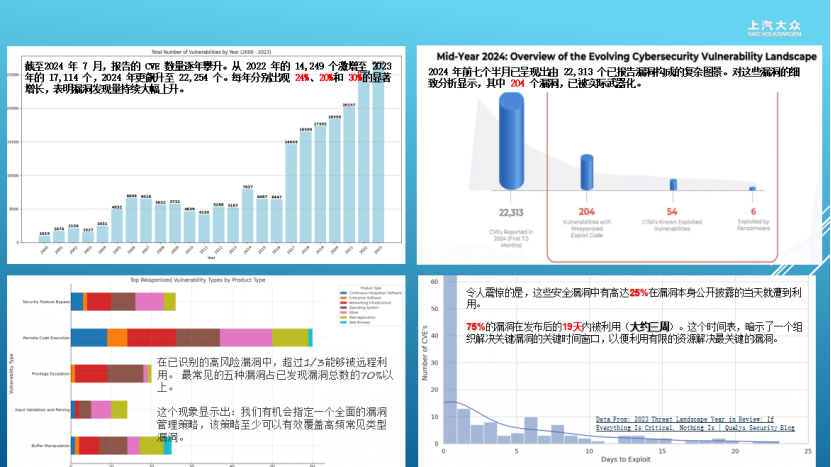
The traditional reliance on passive defense and management measures for vulnerability protection is no longer sufficient to cope with new security threats. Currently, the number of automotive vulnerabilities is on the rise, with 22,000 reported by July 2024, of which 204 have been weaponized. Among the identified high-risk vulnerabilities, more than one-third can be exploited remotely. This situation necessitates a reevaluation and reconstruction of automotive vulnerability protection systems.
Automotive product vulnerability management faces three unique challenges: the scope of impact, with 100% connectivity of new models in China and individual model market ownership often reaching tens of thousands, where a single vulnerability could trigger a large-scale security incident; the degree of harm, where vulnerability exploitation can lead to vehicle loss of control, information leakage, and other direct safety threats, with statistics from 2024 showing that 77.3% of vehicle attacks target system paralysis; and the repair cycle, as automotive systems involve deep coupling of hardware and software, requiring coordination among manufacturers, suppliers, and service providers, with an average time consumption 3-5 times longer than mobile system updates.
The current vulnerability landscape is characterized by explosive growth, with 22,313 vulnerabilities reported from January to July 2024, a 30% increase compared to the same period in 2023, including 204 that have been weaponized. Alarmingly, 25% of vulnerabilities are attacked on the day they are disclosed, and 75% are exploited within 19 days, leaving companies with a very short response window. In terms of vulnerability type distribution, 63% stem from design errors (such as coding flaws in secure boot mechanisms), and 27% arise from input validation deficiencies (due to dependencies on third-party components), with over 100 new vulnerabilities reported in a single day in July 2024, making vulnerability management a core bottleneck for smart vehicle development.
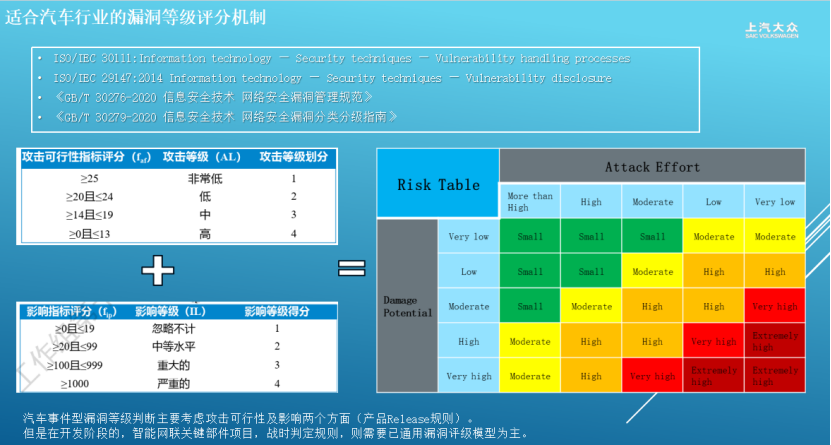
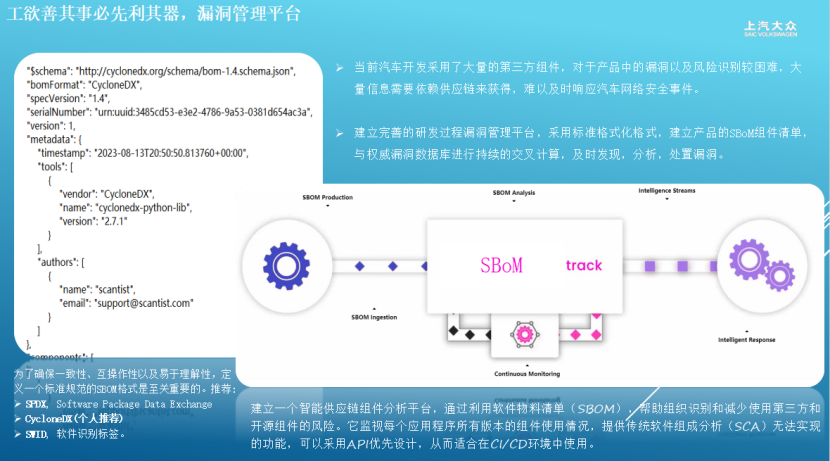
To address these challenges, innovative measures have been proposed, including the establishment of a dual-track rating mechanism and a collaborative defense practice system. In the vulnerability scoring mechanism, the automotive industry cannot directly apply international standards. Mass-produced models will adopt a two-dimensional assessment of 'attack path feasibility + degree of harm' (strictly following GB/T 30279-2020 standards), focusing on factors such as central gateways and firewall deployment; during the development phase, an enhanced general rating that combines ISO 21434 and UN-R155 requirements will be used. Additionally, standardized SBOM management specifications will be established, mandating the use of CycloneDX format and customizing metadata fields to fully address the identification errors caused by traditional Excel management.
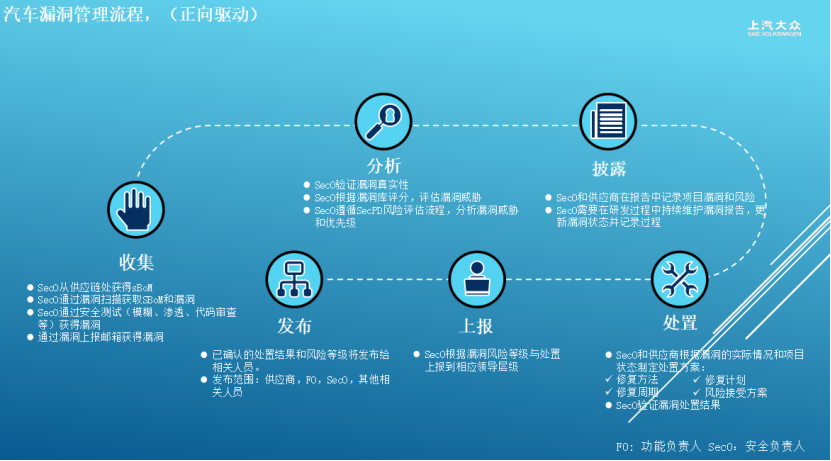
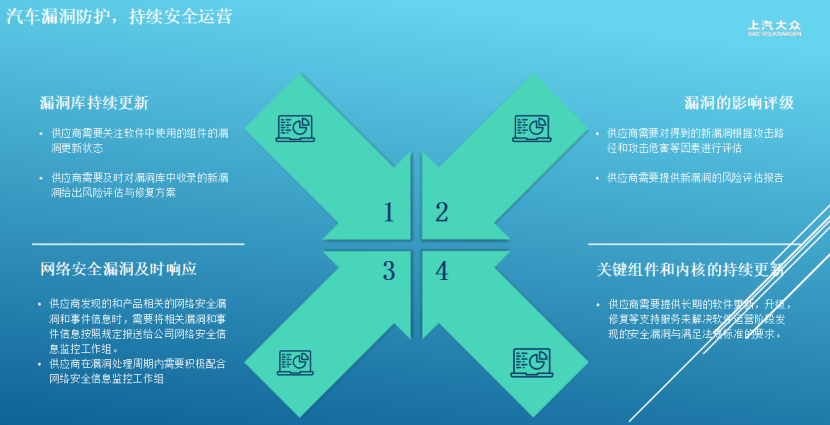
The innovative implementation of a forward and reverse collaborative defense practice system establishes a dual-driven mechanism: the forward end creates a full-link vulnerability management platform, requiring suppliers to submit SPDX format SBOM lists, and using automated tools to link with authoritative vulnerability databases such as CNVD/CNNVD, creating a closed-loop process of 'collect-analyze-dispose-verify', with key breakthroughs including setting a 19-day response red line and initiating a 48-hour emergency mechanism for weaponized vulnerabilities; the reverse end employs firmware scanning technology to reverse engineer ECU binary files, focusing on monitoring high-risk components such as VIVO.
This system achieves three core capabilities: dynamically constructing component dependency diagrams (accurately identifying nested dependency vulnerabilities), establishing a dedicated automotive vulnerability feature library (collecting over 150,000 vehicle-grade vulnerability data), and monitoring core components (covering mainstream high-frequency vulnerabilities).
In the face of an average of 100 new vulnerabilities daily, technological evolution focuses on three dimensions: promoting memory-safe programming languages at the source (gradually replacing high-risk modules written in C language), strengthening the four-eye review mechanism (bringing security design reviews forward to the requirement stage), and constructing a shared responsibility model across the industry chain (jointly establishing a vulnerability repair fund), while developing kernel hot update technologies; on the architectural level, deploying active defense systems in vehicles and developing secure operating systems to achieve vulnerability virtualization isolation. The current core contradiction in the industry is that the GB 44495-2024 standard focuses cybersecurity responsibilities on manufacturers, while many vulnerabilities actually originate from the supply chain. There is an urgent need to promote three foundational constructions: improve national standards for vehicle-grade vulnerability scoring, create public repositories for secure components, and formulate compliance incentive policies for white-hat hackers to address the expected challenge of over 30,000 new vulnerabilities by 2025.
Future challenges and outlook still face ambiguities in defining responsible parties and legal risks associated with vulnerability disclosure. It is recommended that the industry jointly build three foundations: vehicle-grade vulnerability scoring standards, public repositories for secure components, and compliance incentive mechanisms for white-hat hackers. Only by constructing a full-link protection system encompassing 'design-development-operations' can we meet the severe challenges posed by the estimated 32,600 new vulnerabilities expected in 2025.
The Urgency of Addressing Automotive Cybersecurity Vulnerabilities

Images

Share this post on: